How to Build a Voice Authentication System with VAPI AI Effectively
How to Build a Voice Authentication System with Vapi AI: A Security-First Guide
In a world where security and user experience must live together, voice authentication with Vapi AI is the answer. By using the uniqueness of human voice patterns, you can have robust security and a frictionless user experience. This guide will take you through building a voice authentication system that balances security, usability and reliability. Vapi AI offers advanced features that enhance user experience and project functionality.
Introduction to Vapi AI Voice Authentication
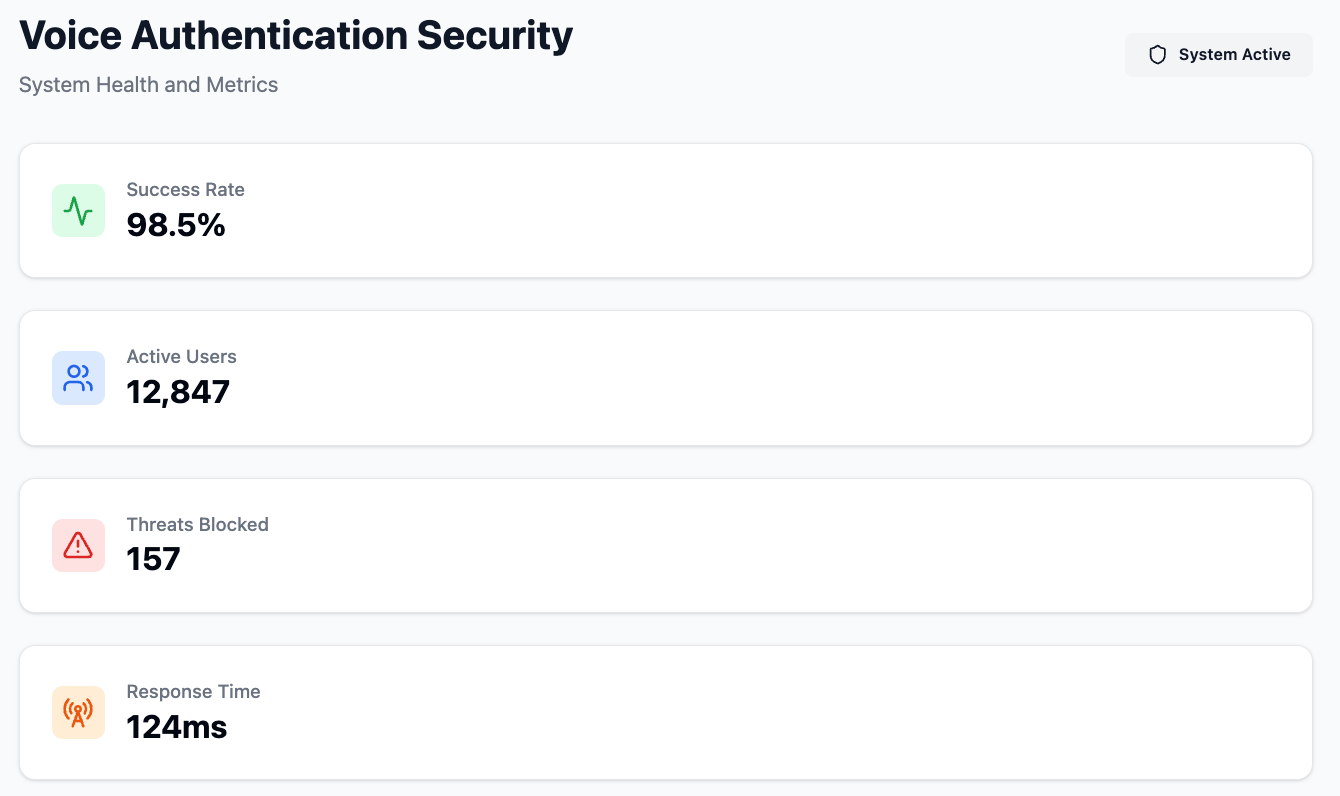
Vapi AI Voice Authentication is a cutting-edge feature that enables secure and efficient voice-based authentication for various applications. By leveraging advanced natural language processing (NLP) and machine learning algorithms, Vapi AI can verify the identity of users through their unique voice patterns. This technology eliminates the need for traditional passwords or PINs, providing a seamless and secure user experience. Integrating Vapi AI Voice Authentication into your systems ensures robust security while maintaining user convenience, making it an ideal solution for modern authentication needs.
Voice Authentication: The Basics
Voice authentication, also known as voice biometrics, uses the uniqueness of an individual’s voice as an identifier. This includes physical attributes (like vocal tract shape) and behavioral patterns (like speaking rhythm and accent). When used with Vapi AI’s technology, voice authentication can be a secure and user-friendly way to verify identity.
Building Your Voice Authentication System: A Holistic Approach
1. Planning
Before you start, define your goals and requirements:
-
Security level requirements
-
Use cases and user scenarios
-
Scalability and performance
-
Accuracy and reliability targets
-
Compliance requirements
Technical Implementation with Vapi AI and Natural Language Processing
Get Started
Start with the basics:
-
Create your Vapi AI project
-
Set up development environment
-
Security setup
-
API setup: Ensure you obtain your API key after account creation. The API key is crucial for authentication and proper configuration of your applications. It helps in accessing Vapi AI services and avoiding common error messages.
-
Monitoring tools
Voice Profile Management
Build voice profile systems:
-
Enrollment process
-
Voice sample collection
-
Feature extraction
-
Profile storage
-
Update mechanism
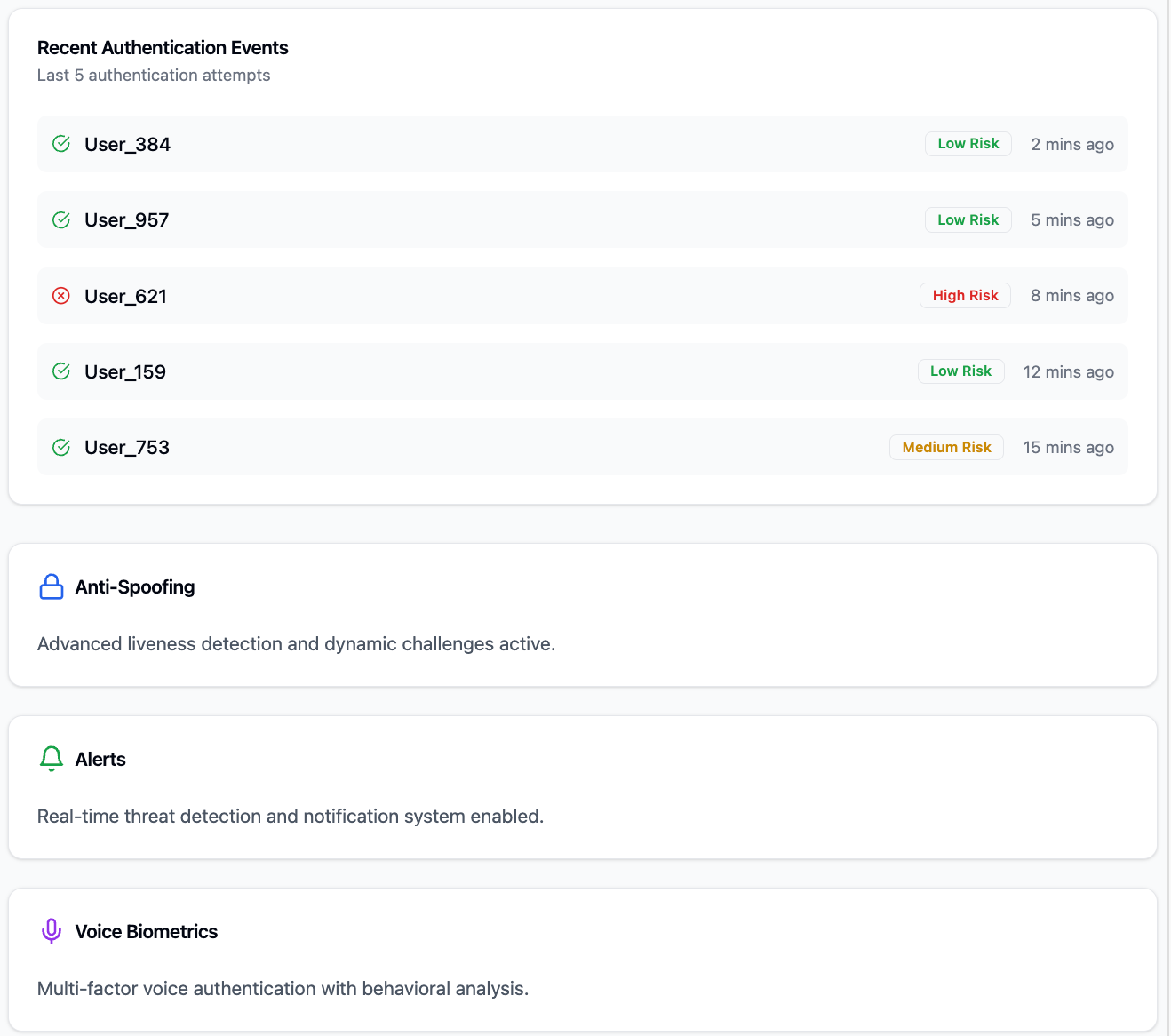
Authentication Flow
-
User prompts
-
Verification steps
-
Anti-spoofing
-
Multi-factor
-
Failure handling
-
Clear and concise language
Security
Core Security
Implement the basics:
-
Encryption
-
Data storage
-
Access control
-
Audit logging
-
Threat detection
Anti-Spoofing
Protect against voice replay:
-
Liveness detection
-
Dynamic challenges
-
Pattern monitoring
-
Behavioral analysis
-
Risk scoring
Understanding Natural Language Processing (NLP)
Natural Language Processing (NLP) is a subfield of artificial intelligence that focuses on the interaction between computers and humans using natural language. NLP enables computers to understand, interpret, and generate human language, facilitating more intuitive and human-like interactions. In the context of Vapi, NLP powers the voice assistant’s ability to comprehend and respond to user queries effectively. This capability is essential for creating a seamless user experience, as it allows the system to process and understand spoken language accurately, making interactions more natural and efficient.
Integrating Vapi with Other Tools
Integrating Vapi with other tools and platforms is a straightforward process that can be achieved through the use of APIs. By integrating Vapi with existing systems, developers can automate tasks, gain valuable insights, and enhance customer interactions. For instance, integrating Vapi with a CRM system can enable automated call logging and lead tracking, while connecting it with a marketing automation platform can facilitate personalized customer engagement. These integrations not only streamline operations but also provide a more cohesive and efficient workflow, ultimately improving overall productivity and customer satisfaction.
Get the Most Out of It: Key Benefits
Security
-
Biometric identifiers
-
Multi-factor
-
Real-time threat detection
-
Continuous authentication
-
Fraud prevention
User Experience
-
Frictionless authentication
-
Natural behavior
-
Fast verification
-
Reduced cognitive load
-
Consistency
-
Concise language
Operational Efficiency
-
Reduced support costs
-
Automated verification
-
Scalable
-
Lower maintenance
-
Higher throughput
Compliance and Trust
-
Strong security
-
Privacy
-
Compliance
-
Transparency
-
Trust
Use Cases
Financial Services
-
Transaction authorization
-
Account access
-
Payment verification
-
Service authentication
-
Fraud prevention
Customer Service Centers and Customer Interactions
-
Caller verification
-
Service authorization
-
Identity confirmation
-
Account management
-
Security escalation
Healthcare
Protect sensitive data with:
-
Patient authentication
-
Record access
-
Prescription verification
-
Staff authentication
-
Secure messaging
Enterprise Access
Secure company resources with:
-
Remote access authentication
-
System login
-
Resource authorization
-
Meeting authentication
-
Document access
How-to’s: Integrate Vapi
1. Enrollment
Design the enrollment experience:
-
User instructions
-
Multiple samples
-
Quality checks
-
Verification testing
-
Profile confirmation
2. Authentication Flow
Build the verification process:
-
Dynamic challenges
-
Multiple steps
-
Contextual authentication
-
Fallbacks
-
User feedback
3. Security
Implement everything:
-
End-to-end encryption
-
Secure storage
-
Access control
-
Audit logging
-
Incident response
Performance
Accuracy and Emotion Detection
Improve the system:
-
Model updates
-
Monitoring
-
Error analysis
-
User feedback
-
Training
System
Optimize performance:
-
Response time
-
Resource management
-
Load balancing
-
Caching
-
Queuing
Privacy and Compliance
Data
Protect data:
-
Data minimization
-
Purpose limitation
-
Storage restrictions
-
User consent
-
Data deletion
Compliance
GDPR
-
CCPA
-
Industry standards
-
Local regulations
-
Audits
Future Proof Your Deployment
Scalability
Plan for growth:
-
Infrastructure scaling
-
Performance optimization
-
Capacity planning
-
Resource management
-
Load balancing
Technology
Stay current with:
-
AI
-
Security updates
-
Industry standards
-
User expectations
-
Threats
Integrate Vapi with various third-party tools, such as CRMs, automation platforms like Zapier, and telephony systems to enhance the functionality of voice AI projects.
Ensure ease of integration with various platforms, including Google Calendar and GoHighLevel, to create seamless automation workflows.
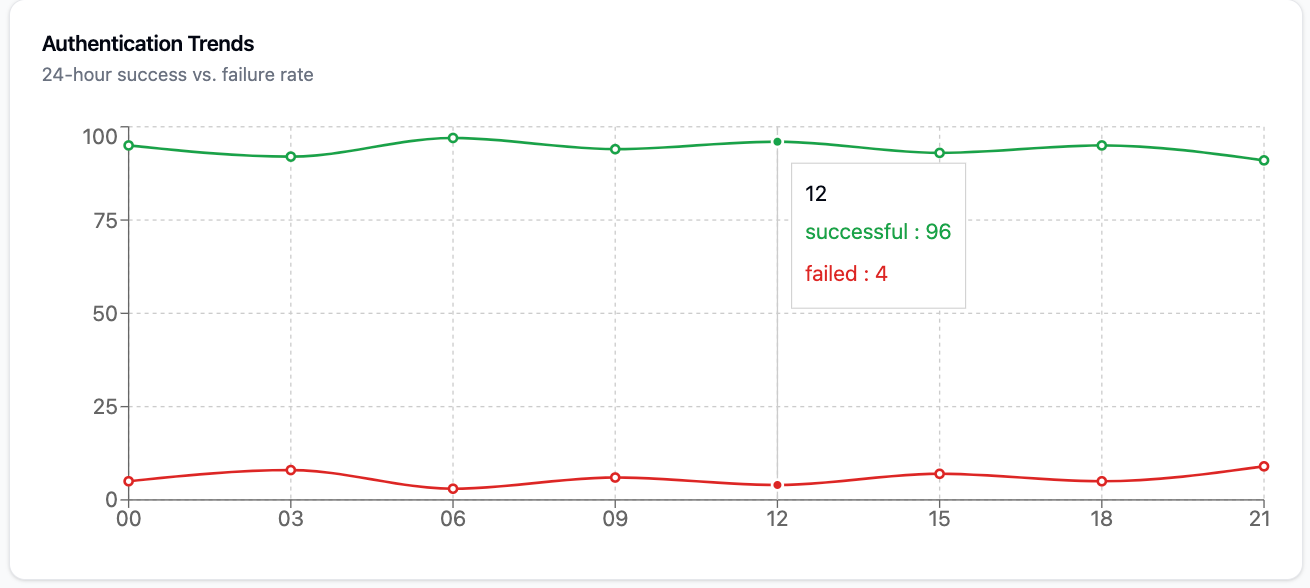
Monitoring and Maintenance
Performance
Monitor:
-
Authentication success rates
-
False accept/reject rates
-
Response time
-
User satisfaction
-
System health
Ongoing Optimization
Update regularly:
-
Patches
-
Features
-
User feedback
-
Tuning
Troubleshooting Common Issues
Troubleshooting common issues with Vapi is made easier through the platform’s comprehensive documentation and robust API. Developers can utilize the API to diagnose and resolve issues efficiently, leveraging the platform’s built-in error handling and logging mechanisms to identify and fix problems. Additionally, Vapi’s customer support team is readily available to provide assistance and guidance on troubleshooting and resolving common issues. This support ensures that any challenges encountered can be addressed promptly, maintaining the reliability and performance of your voice authentication system.
Summary
Deploying voice authentication with Vapi AI is a big step towards more secure and user friendly identity verification. Follow this guide and keep security, user experience and system reliability in mind and you’ll have a robust authentication solution that meets modern security needs and provides a seamless user experience.
Don’t forget to keep security, privacy and user in mind. Start with a solid base, implement everything and monitor and optimize your system. With planning and execution your voice authentication will be a part of your security stack and benefit both you and your users.